Was I just censored by Digg? by ZDNet's Steve O'Hear -- A poll I published asking if Digg users should be paid, hits the front page. Then seconds later it vanishes!
Wednesday, December 13, 2006
Sunday, December 03, 2006
AMD Quad FX slaughtered by a single Intel CPU
AMD Quad FX slaughtered by a single Intel CPU by ZDNet's George Ou -- All the reviews are in for AMD's new "4×4" Quad FX dual CPU platform and it loses nearly every single real world benchmark to a single Intel CPU while consuming more than twice the electricity. We basically see two FX-74 3.0 GHz processors getting slaughtered by a single Intel QX6700 2.66 GHz [...]
What’s the deal with Vista Service Pack 1?
What’s the deal with Vista Service Pack 1? by ZDNet's Mary Jo Foley -- I thought I understood Microsoft's plan of record for Windows Vista Service Pack (SP) 1 ... until I heard CEO Steve Ballmer's Vista business-launch keynote on November 30, that is.
Thursday, November 30, 2006
AMD blasts off Quad for PC DIYers

It has four processing cores; they just don't live together. But Advanced Micro Devices is betting that hard-core gamers won't care about the architecture used to build its new Quad FX Platform.
AMD was expected to launch the new product, formerly known as "4x4," on Thursday via a motherboard built by Asustek Computer. The Quad FX Platform consists of two of the new dual-core Athlon FX-70 series processors connected to two Nvidia chipsets that offer a total of four PCI Express slots for high-end graphics cards, said Ian McNaughton, product manager for AMD's Athlon FX product.
After beating Intel to the punch with new designs over the past few years, AMD is playing catch-up these days. Intel has already launched a quad-core processor for high-end gamers and PC enthusiasts, and the Quad FX Platform is the smaller chipmaker's response to Intel's Core 2 Extreme QX6700 processor, as well as the forthcoming Core 2 Quad processor.
The two Athlon FX processors in the Quad FX Platform sit in two different sockets, unlike Intel's QX6700 chip, which combines two dual-core processors into a single package that sits in a single socket. AMD does not plan to introduce a quad-core processor until the second half of 2007, so it is introducing this platform as a way of providing gamers with high-end processor and graphics performance until it launches those quad-core chips, McNaughton said.
However, because the Quad FX Platform uses two sockets, only the Ultimate version of Microsoft's Windows Vista operating system will be able to take advantage of the second dual-core processor, he said. All other versions of Vista will work on the platform, but won't be able to recognize the second processor. When AMD does introduce quad-core chips designed to fit into a single socket, they will fit into the same motherboard used to build the Quad FX Platform.
PC gamers who like to build their own systems will be the main customers for this product, which basically is an official version of what some system builders have been already doing with AMD's dual-core processors, McNaughton said. But boutique PC companies for gamers, such as Vigor and Cyberpower, will also offer Quad FX Platform-based systems.
AMD is charging $999 for two FX-74 processors, $799 for two FX-72 processors and $599 for two FX-70 processors. The motherboard is expected to cost an additional $300 or so, McNaughton said.
$1,200 keyboard. Nope, it isn’t April 1st!

$1,200 keyboard. Nope, it isn’t April 1st! by ZDNet's Adrian Kingsley-Hughes -- Still looking for some holiday stocking fillers … how about a keyboard? It has 103 keys and can display images on each key using OLEDs (Organic LEDs). Price? If you need to ask the price, this keyboard isn't for you!
Monday, November 27, 2006
Make XP look like Vista!
Make XP look like Vista! by ZDNet's Adrian Kingsley-Hughes -- I've had a number of people ask me what I think of the transformation packs that allow you to make Windows XP look like Windows Vista. I had to be honest and say that I'd never tried to do this because I've been running Windows Vista betas for months. Anyway, the other day I was creating some operating system new images in VMware and Virtual PC and I decided to give it a go.
64 is the new 32
64 is the new 32 by ZDNet's Ed Bott -- Microsoft is pushing full speed ahead on its plans to convert its servers to 64-bit technology. But the same can't be said on the desktop side. Even though every edition of Windows Vista is available in a 64-bit version, none of the retail boxes will contain those bits. So what's holding back the transition?
Gateway tech support: “what wireless security problems?”

Gateway tech support: “what wireless security problems?” by ZDNet's George Ou -- When Gateway tech support was asked for an update to a widely publicized Broadcom wireless chipset flaw, Gateway responded with "there are currently no known issue or documented history on this computer". What's it going to take for hardware makers to wake up to these serious security flaws in their hardware?
Thursday, November 23, 2006
Microsoft Has Scrapped the Defragmenter Display in Vista
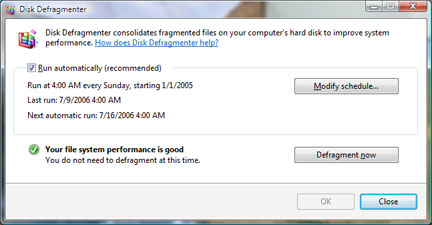
Well, in Windows XP, choose a partition, click Properties, tools and Defragment Now and start the Windows Disk Defragmenter Utility. And, most importantly, don't forget to wave it Good-bye
because the Redmond Company has scrapped the disk defragmenter display in Windows Vista.
With Vista, Microsoft has simplified and automated the Disk Defragmenter tool. “The Windows Vista Disk Defragmenter was simplified primarily for the purpose of removing it out of the face of the user. It runs periodically and keeps your file system fragmentation at acceptable levels, making it unnecessary for you to launch the tool itself. With the new UI, you can see that we really don't want defrag to be something that people have to worry about, just like any number of other low-level capabilities in the OS,” reads a Disk Defragmenter FAQ published back in May.
Microsoft has dumbed down the details from the Defragmenter UI following negative customer feedback, although the interface has survived for approximately a decade. The only objections have been generated by Windows power users, but Microsoft decided to ignore them.
By automating the Disk Defragmenter utility, Microsoft has taken the control out of the hands of the users. The Vista user interface features a check in box for the recommended option to run the utility automatically alongside a “Modify schedule” option. Alternatively, the user is presented with the possibility to “Defragment now.” And... that is it. Aside from changing time and the manually start and stop the defragmentation, the process runs in the background. Microsoft didn't even introduce a percentage-based progress bar, not to mention the bars indicating the Estimated disk usage before/after defragmentation.
Vista BillGates Pirate Edition

While pirated copies of Windows Vista have beaten the
real thing from Microsoft to the market, the Redmond Company has failed to respond in consequence. According to a company statement, Microsoft is attributing “limited value” to the pirated copies of Vista and nothing more.
Meanwhile, Windows Vista, version BillGates is free for the taking. While Microsoft is delivering only Windows Vista Home Basic, Home Premium, Business and Ultimate, crackers have employed all of their creativity when making available Windows Vista BillGates Pirate Edition.
And as the offer of pirated software is often a diversified one, a single pirate website is delivering five different versions of Vista BillGates. In this context, users of pirated software can choose from Windows Vista Final-BillGates 3555103 TPB or Microsoft Windows Vista Final-BillGates 3555203 TPB, with a slight difference of nuance. But Windows Vista Final BiLLGATES is also available, although it seems that Microsoft Windows Vista Final Ultimate Edition-BillGates has drawn in the largest volume of downloads. All the versions come complete with product key and activation patches.
Windows.Vista.Iso.BillGates.To.Legit.MSDN.PATCH and Windows.Vista.Iso.BillGates. To.Legit.Fixed all Bugs.Final Version are Vista patches.
But where is Microsoft in all this? The Redmond Company has adopted a passive approach to Windows Vista piracy. In fact, the Redmond Company is doing little to convince users of the risks associated with deploying pirated copies of Vista and letting its Software Protection Platform deal with the problem.
The Evolution of the Windows Boot Screen

There are many areas in the line of operating systems from Microsoft where the products' evolution can be evaluated. And there have been many evolving stages across a 21 years
Windows history. One aspect that closely reflects the evolution of the Windows operating systems is the Boot screen.
Windows 1.01 was released in November 20, 1985. It was Microsoft's first product designed as an operating environment. No elements of design, except maybe the first “O” in Microsoft, just plain text. Windows 3.1 succeeded version 3.0 and was released in 1992. It features the Windows Logo and the “O” from Microsoft has returned to normal.
Windows 95 was made available on August 24, 1995. The internal codename of the operating system was Chicago and it combined MS-DOS and Windows. The Windows 95 Boot screen introduced the clouds image. Windows NT 4.0 RTMed on July 29, 1996 and was a 32-bit OS designed for workstations and servers.
Remember Memphis? It was the codename for Windows 98. The operating system was released on June 25, 1998, an update, Windows 98 Second Edition was launched on May 5, 1999.
With Windows 2000 (Win2K), Microsoft turned its face to the corporate environment. Windows 2000 hit the shelves on February 17, 2000. Windows Millennium Edition shipped just seven months after Windows 2000. It was the first time Microsoft had integrated Windows Media Player in its operating system.
On October 25, 2001, Microsoft introduced Windows XP, codenamed Whistler. On August 6, 2004 Microsoft released Windows XP SP2, codenamed Springboard. Windows Server 2003 followed in the line of Windows 2000 Server.
And last but not least: Windows Vista. With two separate Boot screens. One with a scrolling bar and the other with the Vista logo associated with the 4 second long start-up song.
Birmingham kills desktop Linux project citing runaway expenses
Birmingham kills desktop Linux project citing runaway expenses by ZDNet's George Ou -- The City Council of Birmingham England terminated a desktop Linux project that was originally planned for 1500 desktop computers in libraries across the city. The reason given for the termination was the high cost of deploying and maintaining Linux. Open source advocates criticized the decision that Birmingham had botched the deployment while Microsoft maintained that it was cheaper to manage Windows.
Calif. court ruling seeks to protect bloggers, Web publishers
The unanimous ruling appears to be the first to make clear that a 1996 law called the Communications Decency Act protects not only providers, but also users of online services who redistribute content. Earlier court rulings had established that Section 230 of that statute shields companies such as AOL and eBay from such liability, provided that they make good faith efforts to restrict access to material that could be considered "obscene, lewd, lascivious, filthy, excessively violent, harassing, or otherwise objectionable."
By passing that law, Congress "has comprehensively immunized republication by individual Internet users," intending "to protect online freedom of expression and to encourage self-regulation," the justices concluded in their majority opinion (click for PDF) penned by Associate Justice Carol Corrigan.
The justices acknowledged that "recognizing broad immunity for defamatory republications on the Internet has some troubling consequences." But unless Congress revises the law, anyone who claims to be defamed by an Internet posting may seek damages only from the "original source of the statement," they wrote.
That protection should not extend, however, to users who conspire with the originators of libelous content, Associate Justice Carlos Moreno wrote in a concurring opinion.
"One engaged in a tortious conspiracy with the original information content provider is hardly one of the neutral 'intermediaries' that Congress intended to absolve of liability," he wrote, adding that he did not believe that sort of activity took place in the case at hand.
The case dates back to 2000, when two doctors who operated Web sites devoted to exposing health frauds sued Ilena Rosenthal, director of a foundation for women and founder of a decade-old Internet newsgroup for women who have had problems with breast implants.
Dr. Stephen Barrett, who runs the site Quackwatch, and Dr. Terry Polevoy accused Rosenthal and others of committing libel "by maliciously distributing defamatory statements in e-mails and Internet postings, impugning plaintiffs' character and competence and disparaging their efforts to combat fraud," according to the state Supreme Court opinion. In particular, Rosenthal had republished on two newsgroups a report by another author who accused Polevoy of stalking a Canadian radio producer.
A California state court sided with Rosenthal, but an appeals court determined that Rosenthal should be held liable as a "distributor" of the allegedly defamatory information.
In the offline world, common law makes a distinction between "publishers," such as newspapers and books, and "distributors," such as newspaper vendors and book sellers. Distributors are considered liable only if they were given notice of a defamatory statement in their merchandise.
But transferring such distinctions to the online world could chill free speech, the state Supreme Court ruled. "The volume and range of Internet communications make the 'heckler's veto' a real threat under the Court of Appeal's holding," the justices wrote.
The high court said it based its decision on a string of earlier cases that immunized online service providers. Perhaps most famously, federal courts found AOL was not liable in a suit first brought in April 1996 by a man named Kenneth Zeran, who claimed the company did not act fast enough to remove defamatory postings directed at him. The same provision of the law also led courts to side with eBay in 2001 amid claims that the online auctioneer should have been doing more to vet the authenticity of sports memorabilia offered by its sellers.
Rosenthal's position had drawn supporting briefs from Internet service providers, law professors and advocacy groups like the American Civil Liberties Union and Electronic Frontier Foundation.
EFF attorney Lee Tien, who co-authored the San Francisco-based group's 2004 brief, applauded the ruling, but said the case never should have had to reach the state Supreme Court level.
"It's so patently obvious that users are protected by the plain language and policy of 230," he said in an e-mail interview.
Tuesday, November 21, 2006
Helmet-cams help police crack down on crime
Officers in Haringey will use the cameras to gather digital images that can then be used as evidence at court proceedings.
The cameras will first be used as part of the five-day Operation Aventail, which will be carried out by the borough's Safer Neigbourhood unit and focus on antisocial behavior.
"Should anyone commit any offenses the officers will instantly have the evidence to hand to help them apply for an ASBO (antisocial behavior order) or pursue criminal charges," Detective Superintendent Richard Wood, head of the operation, said in a statement.
The cameras are similar in size to an AA battery, and the images are stored on a special utility belt. The kit costs around $3,402 (1,800 pounds) per officer and has been funded by Haringey Council's Safer Communities Partnership.
Wood added that if the cameras prove successful they will be used by other Haringey units and could assist in police raids or police presence at soccer matches.
The unit is using several other tactics as part of Operation Aventail. These include airport-style weapon searches, automated license-plate recognition technology (to identify stolen vehicles), targeting of crime hot spots, and increased visibility for patrols.
Small companies ignorant of security?
Speaking at an IT security event at London's House of Lords on Monday, Schmidt said all businesses are at risk through a lack of proper configuration of security equipment, or through not taking proper security precautions.
"SMEs (small and midsized enterprises) are not aware of being a potential victim--spending 40 pounds per year on antivirus is not a high priority," he said at the event, organized by managed services specialist Claranet. "SMEs have to realize that just because they are small, it doesn't mean they won't be targeted. Bad guys target wherever they can get money."
Ninety percent of small businesses and consumers install antivirus, but 10 percent never update the software's signatures, which are matched against suspected threats, Schmidt said. Small businesses with limited staffing resources simply do not have time to devote to cybersecurity issues, he said.
In addition to keeping a lookout for malicious software, organizations need to be aware of important data leaving the company, often through human error. Employees using file-sharing networks are often unaware of the security implications, Schmidt said.
"Individuals working on peer-to-peer networks often don't realize they're sharing the whole contents of their drive. You can find Homeland Security vulnerability assessment documents online from employees (using P2P)."
However, Schmidt said that SMEs will eventually start using managed software security services, with third-party providers managing both low-cost application level security and end-point hardware.
"Eventually, we'll move to a model of software as a service, with a low-cost environment of managed security services," he said.
However, application software should have security built in from the beginning, said Schmidt, who added that he looks forward to a time when software will be able to configure automatically to a user's system and detect attempted security breaches.
"I don't think the end user should protect themselves. It's like safety in new cars--built in. They want automatically self-healing and self-configuring software," said Schmidt.
Small businesses must take security into account in their planning and decide whether to outsource security, invest in training or allocate more resources. "Training is important, because we don't know what we don't know," Schmidt said.
If a small enterprise does have a full-time IT manager, that manager should become familiar with security standards such as ISO 17799, he said. "IT managers need to follow best practices--they should know what security applies to which devices. The trouble is, many times they're far too busy," Schmidt noted.
Charlie McMurdie, a detective chief inspector in the computer crime unit of the Metropolitan Police in London, said that "SME security is disjointed at the moment."
McMurdie said that computer security should follow common-sense procedures. "If you had a house, what traditional measures would you have around the premises? Who has a key? People need to apply the same common sense to Internet security. Stand back and look at who has access, who has a password."
Schmidt is on the board of directors for Fortify, which sells source code analysis tools.
Justice Dept.: Vista satisfies antitrust deal
In a periodic joint status report, required as a part of Microsoft's 2002 antitrust settlement with the U.S. Department of Justice and state plaintiffs, the government attorneys said a technical committee charged with overseeing the software giant's compliance had found no outstanding issues after "extensive testing" of Vista and Internet Explorer 7.
According to the report, Microsoft and the technical committee have been offering a downloadable program that is designed to help Microsoft's competitors in the fields of Web browsers, e-mail and instant-messaging clients, and media players to make their programs "Vista-ready" before the new operating system ships.
The program serves as a single source for all the registry settings needed for applications "to attain equal visibility on Windows XP and Vista systems," the technical committee said. The program's goal is to reduce the chance that people will experience difficulties in changing default software to non-Microsoft products, for instance. It also aims to make it easy to locate third-party applications in the start menu, desktop, task pane and other commonly used surfaces, after installing them.
Microsoft said it had also contacted 30 competing software makers and had invited them to work alongside company engineers at its Redmond, Wash., campus lab for Vista Readiness.
Since the last status report filing in May, government attorneys said they received 25 complaints alleging antitrust concerns about competing middleware but said they concluded that none of those gripes had merit.
Although the matters were not raised by U.S. regulators, some possible antitrust repercussions of security and file-formatting features in Vista were recently flagged as concerns by European and Korean regulators. Microsoft said last month that it had implemented changes that address those complaints.
The latest status report said Microsoft appears to be making some progress on what has become one of the thornier components of the settlement: rewriting documentation for licensees of its Microsoft Communications Protocol Program. The MCPP, another requirement of the antitrust settlement, is designed to help third-party developers create software that works with Windows.
But government attorneys said they remain worried about the project staying on track. Microsoft has already endured scolding for alleged "foot-dragging" on that front from the plaintiffs and the federal judge presiding over the case, who ultimately approved a two-year extension for that project's deadline.
"Microsoft's full commitment will be essential if the project is to stand any chance of producing complete and accurate documents on the schedule that Microsoft has provided to the court," the government wrote in its portion of the status report.
In a separate battle in Europe, Microsoft faces a Thanksgiving Day deadline for completion of a similar documentation project.
Monday, November 20, 2006
'Tis the season to send spam

In addition to plenty of turkey, a record amount of spam will be served up this holiday season.
Mass e-mailers traditionally bump up their activity as the year winds down. But this year, the amount of junk messages could be unprecedented, companies that make spam-busting tools say. And senders of unsolicited ads are already celebrating the close of the harvest season and the approach of Christmas.
"Just as legitimate vendors began stocking their shelves with holiday decor and gifts before Halloween, spammers started sending spam messages tailored to the holiday gift-giving season earlier this year," said Stephen Pao, vice president of product management at Barracuda Networks, a Mountain View, Calif., maker of security appliances.
In October, 63 billion junk messages were sent daily, on average, compared with 31 billion a year ago, according to data from IronPort Systems. Another antispam specialist, MessageLabs, reports that 88.7 percent of all e-mail sent in October was unsolicited. That percentage is expected to rise to nearly 90 percent in November and December.
That could add up to a huge pile of unwanted e-mail. IronPort predicts that the number of spam messages will average 78 billion a day in December, up from 38 billion last year.
Internet service providers and antispam companies are working hard to fight this onslaught of spam. But it's a game of cat-and-mouse, and right now, the spammers are slipping away, experts said. "The antispam vendors are struggling," said Natalie Lambert, an analyst at Forrester Research. "The best vendors are able to stop about 98 percent of spam." That still leaves 2 percent that gets through, which is a lot with the current, increasing spam levels, she added.
There's a holiday spam spike every year, because people are more likely to open the messages, experts said. Consumers are shopping online more, are desperate for gift ideas and expect electronic greeting cards. Spammers exploit all of that by sending fake order confirmations and e-cards and, of course, suggesting their products as gifts.
"People sell fake Rolexes via spam e-mail, and fake Rolexes make good holiday gifts," Pao said. "We expect that the amount of overall holiday-related spam to increase up to 50 percent during the week of Thanksgiving and continue through New Year's. It looks like this could turn out to be the largest, and longest, holiday spam season ever."
New tricks
There are a number of reasons for the rising tide of messages, experts say. For one, spammers are constantly looking for and finding new ways to reach unsuspecting people, said Miles Libbey, a product manager at Yahoo. "We continue to work tirelessly to make sure junk mail goes into the spam folder," he said. Yahoo, which operates one of the most popular free e-mail services, is using technology and collaborating with others to bust spam rings, Libbey said.
Technology advances are another driver. Spammers are using new tools to relay messages via networks of compromised, broadband-connected PCs called botnets. That means lot of the messages in that glut are being sent via PCs owned by unsuspecting people, who are probably busy eating their turkey and ham while the e-mail is being sent out.
At the same time, the mass-mailers have found new ways to circumvent filters meant to weed out unwanted messages. It's a perfect storm for spammers, experts said.
"During October, we started to see unprecedented spam levels--much higher than we have seen in previous years. This seems to be on the back of a Trojan that is much more robust," said Mark Sunner, a chief technology officer at MessageLabs.
A lot of the messages are being delivered using the new Trojan horse, called "SpamThru", which surfaced recently, Sunner said. Such malicious software typically gets onto Windows PCs via malicious Web sites or as an e-mail attachment disguised as something the user might want--a screen saver, for example. It may also creep onto a PC unbeknownst to the owner by exploiting a security hole.
"The technique is referred to as a spam cannon," Sunner said. "In a traditional botnet, the bot herder would connect to the network and send out spam messages one-by-one, kind of like a pea shooter. By contrast, SpamThru works like a mail merge."
SpamThru is unique because it uses peer-to-peer technology to share information with other compromised PCs. That information includes details on the control server, spam templates and all the peers each compromised computer knows about, a researcher at security company SecureWorks said.
The Trojan horse appears to be the handiwork of Russian programmers, SecureWorks added. Researchers found evidence that about 73,000 computers in 166 countries are part of the SpamThru botnet, adding up to a mighty spam cannon.
Avoiding blocks
At the same time, junk e-mailers have gotten better at tricking filters, experts said. The latest techniques rely on e-mails that are simple text or that carry only an image. In the pure text messages, key words are often misspelled to throw off filters. The image-based junk is tough to sift out, because many spam filters can't see what's in the image.
"Sophisticated spammers generally design and test their messages against the current spam definitions of popular spam filters," Pao said.
All that unsolicited e-mail eats up a lot of bandwidth and can clog e-mail servers, not to mention inboxes. Last month, all the spam sent worldwide added up to 819 terabytes per day in data, compared with 275 terabytes a year ago, according to IronPort's research.
"The problem is that spam filters, even very good ones, catch a certain percentage of the spam. Even if they catch 99 percent of the spam, 1 percent of a big number can still be a very big number (of e-mails that do make it through)," said Tom Gillis, senior vice president of worldwide marketing at IronPort in San Bruno, Calif.
The economic impact from time wasted deleting spam was estimated to be $21.6 billion in 2004, according to the National Technology Readiness Survey, an annual survey conducted by Center for Excellence in Service at the University of Maryland's Robert H. Smith School of Business and Rockbridge Assoc.
"E-mail users are getting very frustrated, and ISPs and enterprises are paying for a lot of bandwidth," Forrester analyst Lambert said.
The continued increase in spam and the challenges of dealing with it suggest that Microsoft Chairman Bill Gates' prediction two years ago, that the spam problem would be solved by now, has not come true. "Spam is definitely a continuing problem," Lambert said.
Spam fighters haven't thrown in the towel. Companies such as Barracuda Networks, IronPort and MessageLabs are working to strengthen their spam filters. At the same time, e-mail service providers and Internet service providers such as Yahoo are trying to keep consumer in-boxes clean through technology and initiatives such as Sender ID and DomainKeys Identified Mail.
For now, though, it looks like people will be getting a lot of junk in the Christmas season.
"The amount of spam has been increasing over the past year--especially around the holidays. Really, it will only get worse," Lambert said.
Windows Vista available to developers
After years of development work and a last flurry of testing, Microsoft finalized Windows Vista last week.
On Thursday, Microsoft made the code for Vista available to subscribers of the MSDN and TechNet developer programs, a milestone that was noted on a number of Windows enthusiast sites.
The software maker plans to offer Vista and Office 2007 to volume license customers on November 30, while consumers will have to wait until January for the latest versions of Microsoft's flagship products.
Meanwhile, the company is giving free copies of Windows Vista to members of its technical beta program who filed at least one bug report during the testing of the operating system. The offer does not apply to technology enthusiasts who downloaded Vista as part of the broader Customer Preview Program.
Sunday, November 19, 2006
Next 100 visits
Friday, November 17, 2006
SANS names top hacker targets
The SANS Institute also said Wednesday that Microsoft Office and Windows Libraries and Services are some of the most vulnerable applications available on computers today.
But Microsoft was not alone in the annual list, released Wednesday. Apple Computer's Mac OS X was also cataloged, along with "configuration weaknesses" in Unix.
The 2006 list is of the Top 20 Attack Targets, whereas previously it was named the Top 20 Internet Security Vulnerabilities. Written by members of the SANS Institute and security experts from the technology industry and government bodies, it indicates which network features could leave a company vulnerable to attack.
Rohit Dhamankar, the chief scientist at TippingPoint and a SANS member, explained some current security threat trends.
"We've seen a lot of zero-day vulnerabilities this year. The next big thing is the number of attacks on Web applications. There's also continued growth in 'spear-phishing' attacks from Asia and Eastern Europe." In spear-phishing, the attacker creates an e-mail that appears to be a corporate internal message and sends it to a specific group of people in that company, who may be lulled into opening its malicious payload.
SANS also named Web applications, peer-to-peer (P2P) file-sharing software, media players, VoIP (voice over Internet Protocol) phones and people themselves as some of the easiest targets for hackers.
The Web grows up
The Web grows up by ZDNet's Phil Wainewright -- The news that American Express has launched an 'intelligent online marketplace' based on hosted technology from Rearden Commerce reinforces many of the themes I've been writing about recently.
AMD designs prototype PC for the living room
Resembling a stereo component, the computer is designed essentially to function as a media vault: it stores music, videos, TV shows and photos, and then pipes them to flat-panel TVs and other PCs. PC makers can, conceivably, use the prototype as a reference design.
"There will be PCs in the living room. They won't look like PCs," Joe Menard, corporate vice president of consumer business at AMD, said during an interview at the Samsung Executive Summit this week in San Jose. Some of these types of PCs may come out next year, he added.
Companies that have tried to get PCs into the living room include Gateway and Compaq, which tried to sell large-projection TVs linked to PCs in the late 1990s. But high prices led to low sales.
In early 2004, Intel's Paul Otellini unfurled the EPC (Entertainment Personal Computer) at the Consumer Electronics Show. Its bulky appearance and noisy fan crimped sales. Intel revamped the idea with its Viiv line of PCs. Still, most Viiv PCs are not packaged in sleek, small cases that would fit in living-room entertainment racks. Most Viiv PCs are about the same size as standard desktops and laptops.
Apple Computer also came out with a Mac Mini in 2005, but despite the good reviews, it's nowhere near being a cultural phenomenon.
There are Intel-based computers making it into the living room, but they're not PCs. Toshiba's HD DVD player runs an x86 chip. Some set-top boxes also have Intel chips.
So why will the living-room PC concept succeed where it has limped along in the past? Chip cooling has improved, so computer makers will be able to get away from fans, Menard said.
With Vista, Microsoft's soon-to-be released new operating system, consumers will be able to play high-definition content on PCs--providing them with an incentive to pick up a living-room PC.
One fantasy that Bill Gates thankfully knows how to fulfill
One fantasy that Bill Gates thankfully knows how to fulfill by ZDNet's David Berlind -- Against the backdrop of all the vendors who've been indemnifying their customers against this, that, or the other lawsuit, I keep telling people that it's highly unlikely that vendors are going to sue you if the software you got from someone else (eg: Red Hat) infringes on a patent that belongs to someone else (eg: [...]
Windows Live Messenger and Windows Vista: Worse together
Windows Live Messenger and Windows Vista: Worse together by ZDNet's Mary Jo Foley -- Now that Vista's done, you might think that Windows Live Messenger and Windows Vista might be coexisting more peacefully. If you did, you would be wrong.
Bosses get into 007 gadgets
Bug-detectors disguised as fountain pens, keyboards that can secretly record everything typed on them, and clock radios with hidden cameras--devices once only of interest to spies--are now being bought by company chiefs who fear they are being spied on.
"The majority of the customers are buying countersurveillance equipment," said Julia Adams, director of surveillance gadget store Spymaster. "The majority are concerned with what is being leaked. They want to make sure they aren't being bugged and that the competition isn't listening."
Some executives carry pocket-size bug detectors when they are in meetings, on their own premises or elsewhere, that vibrate if they pick up on eavesdropping equipment.
Adams said that people usually pay the Spymaster store a visit because they have a feeling that something is not quite right and, as she points out, "more often than not that feeling is correct." Once they have equipped themselves with countersurveillance gadgets, executives often come back and stock up on surveillance devices, so that they can then find out which staff member in their office has been leaking information.
Business chiefs may well be right to watch their backs. According to a survey of 2,000 office workers commissioned by Samsung Electronics, 57 percent of respondents said they have found and read confidential information on a printer, and 21 percent admit to having read confidential information on a colleague's monitor.
And it's not just staff leaking company secrets to rivals that bosses have to watch out for. With the Cold War long over, corporate espionage has been heating up.
According to MI5, as the U.K.'s national security service is commonly known, foreign intelligence services are now targeting commercial enterprises "far more than in the past," in an attempt to get their hands on communications technologies, IT, lasers, optics and electronics, to name just a few targets.
At least 20 foreign intelligence services are operating to some degree against U.K. interests, MI5 warns, trying to get secrets from people by exploiting technology such as communications and computer systems. This means as well as buying countersurveillance gadgets to protect themselves, companies need to make sure their computer systems aren't coming under attack.
MI5 has a list with IT security advice on its Web site. It warns that electronic attacks may come from a range of sources: criminals, foreign intelligence services, lone hackers or terrorists. Companies should conduct a risk assessment to establish whether they are at particular risk of an electronic attack, it warns. Indeed, its sister agency, MI6, recently advertised for techies to help keep its own networks secure.
Other recommendations include:
• Buy IT gear from reputable manufacturers and suppliers.
• Ensure that software is as up-to-date as possible. Consider checking for patches and updates at least weekly.
• Ensure that Internet-connected computers are equipped with antivirus software.
• Always ensure that your information is regularly backed-up.
• Try to ensure that those who maintain, operate and guard your systems are reliable and honest.
• Seek regular security advice from system and service providers and make sure you act upon it. Pre-empt attacks instead of waiting for them.
• If there are particular categories of material you wish to protect, you could consider encryption.
• Take basic security precautions in order to prevent software or other information from falling into the wrong hands. Implement a program of security awareness among your staff. Train them not to leave sensitive material lying around and to operate a clear-desk policy.
• Invest in security cabinets and fit locking doors.
• Ensure the proper destruction of confidential material.
Wednesday, November 15, 2006
10 things you can do to give old servers a second life
To run with the pack in terms of performance, productivity, and competition, servers that are long in the tooth have to be put out to pasture regularly. But there might be (and usually is) some life left in these early retirees, and they can still be put to good use. Often, you can give old servers a new lease on life by upgrading to a bigger hard drive and adding RAM. The nature of your network will dictate what's best for you, but here are some ways you might get additional mileage from an old server.
#1: Turn it into a patch management server
Patch management is the bane of the network admin's life. In a Microsoft network environment, everything--from PowerPoint to Windows Server 2003--needs to be regularly patched for vulnerabilities. Setting all clients (I'm not even mentioning servers) to auto-update is not the wisest decision. Apart from being a waste of bandwidth (so many clients going out on the Net to download the same patches), you might (rightly) not like the idea of surrendering control over what needs to patched and when to some automated process. You need a centrally managed system.
If you're a small to midsize enterprise, you might find the cost of commercial offerings to be too high. A reasonably good--and free--alternative, is Microsoft's Windows Server Update Services (WSUS). You'll find a step-by-step guide to installing, configuring, and using WSUS here. According to the guide, the hardware recommendations for a server with up to 500 clients are a 1 GHz processor and 1 GB RAM.
#2: Create a NAS server for backups
Backups are the other bane (pain!) of the network admin's life. Here, also, that old server can provide relief.
Thanks to some great software available at a very reasonable price, you can quickly and painlessly turn an old server into a network-attached storage (NAS) device. Apart from the software, NASLite-2 CDD, you'll probably just need to add some big drives to turn your old server into a monster backup server. You'll find the software and more info here.
NASLite-2 CDD is bootable from CD as well as USB. As you'll read on the site, "NASLite-2... is optimized to perform at maximum efficiency with minimum of hardware requirements." It boots directly into RAM and runs on a mere 8 MB RAM disk. Basic requirements are a Pentium processor and 64 MB or more of RAM.
#3: Use it for disk imaging
Having up-to-date disk clones (ghost images) of critical machines (and even noncritical ones--e.g., in environments where you have many machines with the same hardware and software) can really save your bacon--and save you time. Finding storage space for these big images is another matter, though. But an old server might do nicely, even if you can't afford the luxury of buying software to re-image network clients from a central server. You can add some big drives to the old server to merely use its capacity to save all the images, which you can then use to re-image from a client (e.g., just copy the image to a removable drive and restore the image from there).
#4: Put it to work as a firewall
In need of a firewall? If writing Cisco access control lists isn't your forte, and your budget doesn't allow for a hardware or commercial software firewall, consider SmoothWall. This is a refined open-source firewall that will give many commercial apps a run for their money.
According to the site, "SmoothWall includes a hardened subset of the GNU/Linux operating system, so there is no separate OS to install. Designed for ease of use, SmoothWall is configured via a Web-based GUI and requires absolutely no knowledge of Linux to install or use."
#5: Make it a test server
Why not use that old server for testing purposes? In a lab/test environment, you don't need top specs. (In fact, testing with minimum specs might be the point of the exercise and could be a good indicator of expected performance.) If need be, just throw in some extra RAM. You can use such a machine for testing new applications and new server offerings or even to practice your "alternative" operating system administration skills by installing Linux, UNIX, or FreeBSD.
Another good idea is to install virtual PC/server software on such a PC. With the competition between Microsoft and VMware heating up, expensive versions of these virtual machines are now available for free. You can get Microsoft's Virtual PC 2004 and Virtual PC 2007 (with support for Vista) here. Virtual PC 2007 was in beta at the time of writing. Microsoft Virtual Server 2005 R2 is also available as a free download. VMware's server offering is available here.
#6: Turn it into a file/print server
If you have a small department with its own needs, an old server can come in handy as a dedicated file/print server, easing the burden on your main file/print server(s). Installing a file server is simple enough. For more on Windows Server 2003 Print Services, see this article.
#7: Create a terminal server
If ever you wanted to try out the capabilities of Terminal Server services (especially the application server features), that old server could be just what you need. Just remember to put in lots of RAM. For a technical overview of Windows Server 2003 Terminal Services, download this Microsoft document.
If you like what you find, check out Deb Shinder's article "Create a scalable thin client solution with Terminal Server farms" for even more inspiration.
#8: Use it as a DHCP server
In the article "Create a superscope to solve the problem of dwindling IP addresses," I wrote about the problem of running out of IP addresses and explained how introducing superscopes could solve the problem. An extra DHCP server to help dish out addresses on another subnet can sometimes come in very handy in this situation.
#9: Make it a mail /SMTP server
So the big boss listened to the Linux guys and dumped Exchange Server. But now he and the rest of management want all the Exchange features and guess what? No can do. But maybe an open source product (there's also a network edition) called Zimbra is the answer. I haven't tested it, but it looks like a real contender, particularly for midsize and smaller companies. Try it on that server you're using for testing! For more information, go to http://www.zimbra.com/community/documentation.html. The requirements for evaluation and testing are an Intel/AMD 32-bit CPU 1.5 GHz, 1 GB RAM, and 5 GB free disk space for software and logs, as well as additional disk space for mail storage.
#10: Convert it to a monitoring server
Call me superstitious, but I like to keep my servers clean and pristine and dedicated to their primary roles. So yes, as a WAN manager I need software to sniff and ping and enumerate resources and to scan and inform me about the state of my network. But no, I'm loathe to install such software on my domain controller or other server performing some dedicated role. That's why I used the first old server to be retired for this noble task.
I gave the job to Spiceworks IT Desktop. (You can read Justin James' review here.) IT Desktop is a free, easy-to-use browser-based solution. You can believe the site when it says that the product takes less than five minutes to get up and running. It's designed for organizations with fewer than 250 devices on their network. System requirements are Windows XP Pro SP2 or Windows 2003 Server; a 700 MHz Pentium class processor; and 512 MB RAM.
You could also put The Dude to work. It does a great job of mapping your network and can be used for pinging, port probes, and outage notifications.
Some of your retired servers may not make the grade. But if you keep in mind these possible uses, I'm sure most of them will be able to perform some of these roles, thus giving new life to a potential doorstop.
Critical Broadcom Windows driver exploit released!
Critical Broadcom Windows driver exploit released! by ZDNet's George Ou -- According to Johnny Cache, this particular exploit is extremely reliable and results in "100% ownage" which means your computer belongs to the hacker if it's attacked using this exploit. Since the exploit has been rolled in to the Metasploit 3.0 framework which includes kernel-level shell code, the exploit can be performed with a moderate amount of hacking knowledge. This flaw is extremely dangerous because it exploits the kernel of the operating system which means it bypasses all conventional security measures like anti-virus, HIDS, firewalls, and user privileges. The attack range is limited to Wi-Fi range which is typically 100 to 200 feet but can be extended with high-powered antennas.
Wednesday, November 08, 2006
Will Windows Vista be worth the wait?
Will Windows Vista be worth the wait? by ZDNet's Ed Bott -- It's been a long and winding road, but Windows Vista is finally released to manufacturing. You'll no doubt be overwhelmed with coverage of the minutiae of Windows Vista in the next few days and weeks, but focusing on the road behind or on pixel-by-pixel inspections is a waste of time. After nearly a year of working with Windows Vista day in and day out in production environments, I've come up with three questions that every Windows user needs to ask about Windows Vista.
Friday, November 03, 2006
Virtualization and confusing array of Vista legal restrictions to haunt Microsoft and users alike
Virtualization and confusing array of Vista legal restrictions to haunt Microsoft and users alike by ZDNet's David Berlind -- According to fellow ZDNet blogger Mary Jo Foley, Vista's licensing is confusing enough. She literally ends up screaming for help. But, over at SecurityFocus, Scott Granneman is drawing attention to some of the more objectionable (and seemingly arbitrary) terms in Microsoft's End User License Agreement for the new version of Windows. In his analysis, there [...]
Thursday, November 02, 2006
Microsoft changes Vista license terms
Microsoft changes Vista license terms by ZDNet's Ed Bott -- Who says Microsoft doesn't listen? Three weeks ago, when the new license terms for Windows Vista were officially release, one change set off an avalanche of feedback from the enthusiast community. Today, Microsoft rewrote that part of the license agreement. Individual users can now transfer a retail license from one PC to another or upgrade an existing computer without fear of being forced to pay again.
Microsoft backtracks on Vista transfer limits

REDMOND, Wash.--Reversing a licensing change announced two weeks ago, Microsoft said on Thursday that it will not limit the number of times that retail customers can transfer their Windows Vista license to a different computer.
On Oct. 16, Microsoft issued the new user license for Vista, including terms that would have limited the ability of those who buy a boxed copy of the operating system to transfer that license. Under the proposed terms, users could have made such a switch only one time.
However, the new restriction prompted an outcry among hardware enthusiasts and others. Microsoft is returning the licensing terms to basically what they were in Windows XP--users can transfer their license to a new PC an unlimited number of times, provided they uninstall and stop using it on the prior machine.
The software maker said it paid attention to the response both directly to the company and on blogs and decided to reverse course. Microsoft had hoped to use the change to aid its ongoing efforts to thwart piracy.
"We're trying to be really clear about our intention to prevent piracy," said Microsoft product manager Mike Burk. "At the same time, after listening to the feedback that came in, (we) felt that we needed to make this change."
By reversing course, Burk said, Microsoft hoped to assuage users' concerns, particularly those of hobbyists who frequently upgrade the components of their PC, in some cases triggering Windows to consider the machine a new PC.
The plan to limit transfers was part of a series of changes to the terms that apply to boxed copies of Vista, not to the license that comes on a new, Vista-equipped PC. Separate rules apply for the versions of Windows installed on new PCs, which is how the majority of buyers get their copy of Windows. Typically, copies of Windows purchased on a new PC cannot legally be transferred to another PC.
Burk said that Microsoft isn't planning to back off any of its other planned licensing changes, including a move related to virtualization, in which a computer runs multiple operating systems, or multiple copies of the same operating system, at the same time.
Under those new license terms, any Windows version can serve as the primary, or host, operating system. However, only the Business and Ultimate editions of Vista can run as guest operating systems in virtualization.
"We're not planning on making any other changes," Burk said. "We'll keep listening to people's feedback."
No Mobile Blogging for Beta Users
I guess this is just another thing that we beta users will have to deal with.
Monday, October 30, 2006
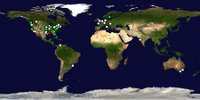
You Have Been Trolled - A Search Word Experiment Final
I would first like to say hello to Mike over in Iraq and for visiting a few times when you can and for giving me some traffic from your blog "The Chronicles of Narmya".
Here is the world map showing the different places I got hits from.

The hits came in from Iraq, Spain, France, Africa, and various places in the U.S.
Well, I will have to think of another trolling post and have some fun later.
Until then,
~Troll
Massive surge in spam hits the Internet
Massive surge in spam hits the Internet by ZDNet's George Ou -- A massive surge of spam has hit the Internet in recent months that appear to be spammers increasing the use of botnets. The spam botnets have grown three times larger since June and they are flooding the Internet spam. TQMcube posted the following chart showing the alarming rise in spam. The red [...]
Vista could cost upgrade enthusiasts serious money
Vista could cost upgrade enthusiasts serious money by ZDNet's Adrian Kingsley-Hughes -- Here's a scary Halloween thought - Upgrading to Windows Vista could see upgrade enthusiasts having to purchase additional licenses. I'm still trying to find out how tolerant or intolerant product activation for Windows Vista is going to be, and to be honest, I don't really feel like I'm getting anywhere.
10 tips and tweaks for Vista experts
10 tips and tweaks for Vista experts by ZDNet's Ed Bott -- Last month, I published 10 tweaks for Windows Vista RC1. It got a good response, but it also drew some complaints. "Too basic," said some critics. "And hey, those aren't all tweaks." OK, fair enough. To satisfy the critics (you know who you are), I present 10 expert tweaks for Windows Vista RC2. No beginner-level stuff here, and I've clearly labeled which are tips and which are tweaks.
Saturday, October 28, 2006
And you thought you got some rain. (Update II)
Friday, October 27, 2006
And you thought you got some rain. (Update)


It is about 8pm CDT and the water is now covering our lower deck. It is too dark to take an effective picture, so I will post one in the morning. I am sure the water will rise another 1/2 to 1 foot by that time.
~Troll
And you thought you got some rain.
You can see from this post where the water usually is on the dock.
These pictures were taken at lunch time. When I left for work there was no noticeable difference in the water level.




Thursday, October 19, 2006
You Have Been Trolled - A Search Word Experiment
If you found your way here through a search engine please leave a comment on which search engine you used. If you feel like it, please let me know what was your search string you entered into the search engine. This might even become a "Who's Who" of search engines. We can all see which search engine is the most popular and maybe even learn of one or two that we haven't heard of yet. Don't be pissed, just have fun with it.
`Troll
*Search strings for 19-Oct-2006*
AOL SEARCH
Paula Abdul, Gas prices, Barack Obama, Heather Mills, The Biggest Loser, Wonder Woman, Patrick Chamusso, Paul McCartney, America's Next Top Model, Tyra Banks, Boots.
cory lidle, north korea, sara evans, friday the 13th, saw 3, the departed, line rider, youtube, mortal kombat armageddon, kim jong il.
Lycos 50
Poker, MySpace, Pamela Anderson, Spyware, Paris Hilton, Pokemon, Halloween, Disney, RuneScape, WWE, Naruto, Golf, Clay Aiken, NFL Football, Colorado, YouTube, Christmas, Baseball, Dragonball, Apple, Wikipedia, Limewire, Britney Spears, Angelina Jolie, Soccer, Barbie, Jessica Simpson, The Rachael Ray Show, Lindsay Lohan, Fashion, Univision, Inuyasha, NBA Basketball, Jessica Alba, Beyonce, Scrubs, Shakira, Jennifer Lopez, Scarlett Johansson, Carmen Electra, Hilary Duff, Eminem, Bit Torrent, Trish Stratus, Christina Aguilera, Anna Nicole Smith, XBox, Final Fantasy, Neopets, Chris Brown.
Yahoo Search
Fear Of Halloween, Second Life, Department Of Energy, Steve Wynn, Heather Mills, Hubble Space Telescope, Environmental Protection Agency, Battle Of Thermopylae, Dionne Warwick, Michelle Williams, Sara Evans, Halloween Costumes, Dancing With The Stars, Second Life, Jessica Simpson, WWE, Justin Timberlake, Beyonce Knowles, Diwali, Deepavali.
Off the top of my head
Love, Sex, freeware, programs, woman, man, women, men, cars, racing, slap, beer, jim beam, laughing, funny, TV, movies.
Sunday, October 15, 2006
The Users of the World Part 1

What makes it possible that a user thinks he/she can do what ever they want on a network?
As they sit there in their pubical all day. Fustrated that the controller has blocked their machine from going to MySpace. (Don't even get me started on that piece of crap site.) They sit there and try to come up with another reason to live through the next week and get to the weekend. This way they can sit in their tiny apartments and live their dismal life away from being plugged into a network.
See at home they are free to do what ever they want. Which is fine with me as long as they don't bring that attitude into the work place. Once you turn on that machine and enter your login and password you now belong to the controller.
This past week there was one such user that thought he was being smart and lost when he under estimated this Systems Administrator. No details, although it would make a great story. I just feel that you shouldn't tell all tales out of school.
My rant is about ALL users around the world. What the hell do you guys think you are doing? Trying to go around the controller's back end. Bringing that stupid iPod and downloading music to it, all the while sucking up bandwidth. The world is splattered with news of lude emails getting sent out to the wrong people, or maybe the right people if you want to come out of the closet on the nations news channels. Laptops are being stolen with all kinds of sensitive data on them. Lord only knows what is going on that we never hear about.
Most data that you users work on his considered company property. Most of that data is considered sensitive or even confidential. You must get really bored and your brain starts to wonder off the track and, poof, you have a problem on your hands. Now the friggin laptop is gone and you just put all those files on it to work at home over the weekend.
Did you ever think to encrypt the data? Nooooo.
Did you even think to lock the laptop in your trunk? Noooo
Did you even think about the events that would take place if anything bad happened when this data was in your hands?NNooooooo
Of course you didn't you are drones, users, sheeple. You have been conditioned not to think about such things. That is why there are Sys Admins and Controllers. We, on a daily basis, think of anything and everything that could possibly go wrong during a 24 hour period and try to put measures in place that will prevent things from happening to the systems or the data. Most times we can prevent bad things. Other times we are fighting with everything we have to beat a problem that is about to ruin our networks. Sometimes we are taken by surprise and ambushed. The ambushes are usually brought on by, you guessed it, the user.
Users can't really be blamed can they? They really have no idea what is going on down in the trenches. Yes they can. They only want to see the geeks when their machine has dropped below mach 1 because of all the spyware they downloaded while playing the stupid flash games. You know the ones, Swat the fly, shoot the illegal immigrants racing across the border.
We sys admins have only one more hole in in the network to plug. That would be the one between the user's ears. For God Sakes start thinking of what you are doing and how it will effect your job. It just might change the way the geeks look at you when they come to fix your machine.
Saturday, October 14, 2006
Blogger Beta The Journey Begins.
I just thought of something. I am blogging about blogger.
Thursday, October 05, 2006
Audio Blogger to shut down Service 11/1/06
As of November 1, 2006, Audioblogger will no longer accept phone
calls. MP3s made with the service will continue to be hosted and
served but you will no longer be able to use Audioblogger to post
new audio.
Audioblogger is an independent product, run by Odeo, Inc., a small
startup company in San Francisco, CA. We are not affiliated with
Google or Blogger except that we operate and provide the
Audioblogger service.
Given our limited resources, we have to make tough decisions
about what projects to focus on. And we've come to the difficult
decision that Audioblogger demands too many resources, time, and
money for us to continue its operation.
However, there are several other services that offer similar
functionality. Odeo is not affiliated with any of these services,
we only suggest them only in hopes that one or the other will be
a good alternative for you.
Gabcast.com is a free service for recording by phone
Hipcast.com has a seven day free trial and lots of features
Gcast.com is another free service for phone recording
All of the phone posting services listed above are compatible
with Odeo in that they produce podcast feeds, which can be
imported to Odeo. Any audio file at Odeo can be posted on a blog
by copying and pasting some embed code.
Odeo would like to extend a huge thank you to everyone who has
tried Audioblogger. If you are interested in keeping up with our
other blog-friendly projects, please have a look at Twitter.com
and our customizable audio players.
Thanks,
The Odeo Team
If any of you use mobiles to post audio to your blog, please let me know what you use. Not that I do a lot of Audio blogging, I would just like the ability to do so when I feel like it. This way I can check them out and get the pros and cons from you all.
Thanks,
Troll.
Saturday, September 30, 2006
Security pros patch older Windows versions
The group, which calls itself the Zeroday Emergency Response Team, or ZERT, created the patch so users of Windows versions that are no longer officially supported can protect their PCs against increasing attacks that utilize a recently disclosed Windows flaw.
The vulnerability, first reported last week, lies in a Windows component called "vgx.dll." This component supports Vector Markup Language (VML) graphics in the operating system. Malicious software can be loaded, unbeknownst to the user, onto a vulnerable PC when the user clicks on a malicious link on a Web site or an e-mail message.
Microsoft rushed out a "critical" fix for Windows on Tuesday to address the problem, two weeks before its regularly scheduled patch day. Microsoft's updates are available for Windows 2000 with Service Pack 4, Windows XP with Service Pack 1 or later, Microsoft Windows XP Professional x64 Edition, and Windows Server 2003.
But Microsoft no longer provides updates for its older operating systems. ZERT sought to fill that void. "A ZERT patch has just been made available for unsupported system versions," the group said on its Web site. The patch has been tested on Windows 98, Windows 98 Second Edition, Windows Millennium Edition, Windows 2000 and Windows 2000 with Service Pack 3, the group said.
ZERT is made up of security professionals from around the world who volunteer their time. Last week the group crafted a patch to plug the VML flaw ahead of Microsoft's fix, so IE users can protect themselves while Microsoft worked on an official patch.
Meanwhile, there are several other security vulnerabilities in Microsoft products waiting to be fixed. Some of these flaws are already being used in cyberattacks, though not as widespread as the VML flaw, according to security experts.
A word of caution is always warranted when it comes to third-party fixes, ZERT has noted. The group does test its fixes, but does not have the same resources Microsoft does when it produces patches. ZERT does provide the source code of its fix, allowing people to validate what it does.
ZERT stresses on its Web site that its fix has no warranties.
Link
Link
Link
Friday, September 29, 2006
Thursday, September 21, 2006
Wednesday, September 20, 2006
Sunday, September 17, 2006
Saturday Night Live (SNL) Clown Penis Commercial
| This is a SNL commercial about a firm that was slow to get a web presence, so they had to settle for clownpenis.fart, the only remaining available domain name. | |
Thursday, September 14, 2006
Sunset

Just had to post the sun setting over the river. After living here just a few weeks, I couldn't be happier with the choice of moving. This picture is what I get to see almost everynight.
-------------------------------
Sent from my HP6515
Thursday, September 07, 2006
10 essential tweaks for Windows Vista RC1
10 essential tweaks for Windows Vista RC1 by ZDNet's Ed Bott -- No, this is not just another set of random Windows Vista screenshots. Now that Release Candidate 1 is available to the public, I've put together detailed instructions for my 10 favorite tweaks, including how to set up Vista without a product key and how to speed up your system without taking the cover off.
Sunday, August 27, 2006
View from new house.

I decided to post a picture to show the view from my porch at my new house. Since I don't have interweb right now, I had to use the mobile.
I have really enjoyed spending the night here. I am not looking forward to my last week in Baton Rouge.
Until next time,
Troll
------------------------------
Sent from my hw6515 PPC
Friday, August 11, 2006
Wednesday, August 09, 2006
robo girl=funny
| Robogirl is the story about a guy who buys a robot girlfriend who'll do anything he askes, except have sex with him. From the ground floor, directed by Steve DePena. | |
Tuesday, August 08, 2006
Blonde riding ponny
| Not your regular Walmart crowd. It sure would be funny to see at Walmart though. | |
In 2021, You'll Enjoy Total Recall

Humans naturally have the power to remember almost two bits of information per second, or a few hundred megabytes over a lifetime. Compared with a DVD movie, which holds up to 17 gigabytes, that's nothing. Worse, you might easily recall the 40-year-old dialogue from Hogan's Heroes yet forget your mom's birthday. Or memorize reams of sports stats while spacing out on work you completed just last week.
It's a problem that's been bothering Gordon Bell for almost as long as he can remember. In 1998 Bell, a senior researcher at Microsoft, began digitally capturing his entire life for a project he calls MyLifeBits. First, he scanned his old photographs, research documents and notes. He began recording his meetings and phone calls and cataloguing his new photos and movies he saw. Every e-mail exchange he had was digitally archived, and he started using the company's prototype SenseCam, which he wears around his neck, to automatically snap photos throughout the day.
Bell now documents about one gigabyte of information every month, all of which is stored in a searchable database on his PC. His is a highly manual process, but he expects that in as few as 15 years it will be common to carry nearly all our "memories" around with us in a single device that will automatically record the sound and video of our daily activities, creating an inventory of the conversations we have, the faces we see and the articles we read. That data would be tied to communications that are already tracked electronically, like e-mail and event calendars, as well as TV shows, movies and other media we take in. The end result: on-demand total recall.
The biggest challenge to Bell's vision is developing the software required to search your memory database effectively. So far, MyLifeBits pulls together more than 20 data types to link various memories to one another. Using a full-text search, Bell tracks down what he's looking for in no more than 30 seconds. Soon, when searching through meeting notes, for instance, photos of people attending those meetings and their contact information will appear side by side. The effort could be pushed along by Columbia University researchers who are using statistical-analysis programs to automatically sort hours of recorded audio by time and location (office, café, etcetera). Next, they'll tackle speaker recognition, which would allow for categorizing and searching conversation by who's talking.
Meanwhile, miniaturization and the falling cost of image sensors and data storage will soon allow for unobtrusive recording, as well as on-person storage, of several terabytes—which means a vast upgrade in personal processing power. "Having a surrogate memory creates a freeing and secure feeling," Bell says of his self-experiment. "It's similar to having an assistant with perfect memory."
Saturday, August 05, 2006
Girl and photocopier - another day at the office
| www.saucyfun.com presents a great clip with a girl and a photocopier, make sure this doesn't happen to you! | |
Microsoft Windows 1.0
| the first windows! This is a funny sales pitch making fun of Windows. Ahh seeing the old interface brings back memories. | |
Sunday, July 30, 2006
Windows Vista Speech Recognition Demo Gone Awry
| Dear aunt, let's set so double the killer delete select all. | |
One Laptop Per Child system - first working prototype
| Demonstration of the first working prototype of the One Laptop per Child computer. | |
Friday, June 30, 2006
The Incredible Shrinking Artwork
Read it here
Wednesday, May 17, 2006
Protect you pr0n!!
In an article over at The Register , there is warning of a new trojan working it's way through the P2P networks.
From the article:
Virus writers have created a Trojan that deletes illicit files from compromised Windows PCs in addition to harvesting data from infected machines.
Erazer-A is spreading (albeit modestly) across P2P networks, where it poses as useful program files, or through chat programs.
Read more here.
Wednesday, May 10, 2006
The Truth Behind the Da Vinci Code
We may have sent rockets into space; we may be able to develop nano-technology and we can even heat up food with micro-wave radiation, but we are still no closer to the truth about our own religions and the secretive organisations that surround them.
The most powerful of them all is of course the Catholic Church and it is this Empire building religion that lies at the heart of the book. To begin with we do need to take a look at the claims made in the Da Vinci Code in relationship to the Holy Grail in-order to understand what the reality of the matter really is.
Read more here.
Rare Mirage Lasts for 4 Hours off East China Shore

Thousands of tourists and local residents witnessed a mirage of high clarity lasting for four hours off the shore of Penglai City in east China's Shandong Province on Sunday.
Mists rising on the shore created an image of a city, with modern high-rise buildings, broad city streets and bustling cars as well as crowds of people all clearly visible.
Read more here
Saturday, May 06, 2006
Japanese develop 'female' android

Japanese scientists have unveiled the most human-looking robot yet - a "female" android named Repliee Q1Expo.
She has flexible silicone for skin rather than hard plastic, and a number of sensors and motors to allow her to turn and react in a human-like manner...
Read More here
video glasses

Read more about them here.
Friday, May 05, 2006
My new 2TB storage for work: The Yellow Machine

When I set it up I will return with a review.
You can find information on this network appliance here.
-------------------------------
Sent from my HP6515
Edit: Updated 08 May 2006
I brought the machine home and found it to be very stout. It has a robust administration interface, either from the installed software on the admin computer or the web interface. I wanted to see how it would reconfigure the Raid, so I configured it to RAID 0+1. The unit calls it RAID 1+0 for some reason. It took about 4-5 hours to complete the transformation. As we are looking for the maximum disk space with a bit of redundancy I reconfigured the YM back to the default RAID 5. If you ever get one of these machines and change it from the default and decide to go back, I suggest you start it and walk away for along time. Try 26-28 hours for completion of the RAID5 configuration.
Tomorrow I bring it back to work and hook it into the network. I had it hooked into my network at the house, but I couldn't see the large share the YM boasts about. I'm sure it is because of the network protocol that I use at home. I remember reading about being able to use the different networking protocols in a few reviews. I just need to play with the YM allot more to find all the settings for such things. All-in-all, I am very impressed with this tiny, breadboxed sized network appliance. I am sure the boss will like it as well, as soon as I get it up and running at the office.
Tuesday, May 02, 2006
Bohemian Rhapsody Music Video
Rock on lil' guy!!
Monday, April 24, 2006
Google Video: "Girl Pwn"
"It's really hard to spin getting wrestled to the ground and pinned by a girl when you're a healthy young guy. I guess ... all you could always try the excuse that she's hot, and you wanted her in that position for a reason."
I truely think this guy is fighting too hard to use such an excuse. Come on man!! Be a man and nibble her goodies!!
Tuesday, April 18, 2006
Microsoft Security patch cripples HP computers
Read the rest from The Register.
Wednesday, April 12, 2006